Terrorist communication
Covert channels (Figure 2) are defined as a resource of communication used to illicitly transfer information in a manner that is breaking the security policy of the system (Ezekiel, Wolfe, Trimble and Oblitey 2005). There are two types of covert channels that can be used: storage covert and timing covert channels.
Covert channels operate on top of existing communication resources (overt communication channel between two overt parties) and embed malicious messages with various methods into the communication stream or leak confidential data, for example by including message bits in the protocol header (storage covert channels) or varying the rate of packet transmission (timing covert channels). These communication channels can easily be exploited by terrorists to exchange information without being detected by cyber-intelligence services or network security elements (e.g. firewalls). It is therefore very important to detect, eliminate, and disrupt covert communications, as they can be a severe security concern.
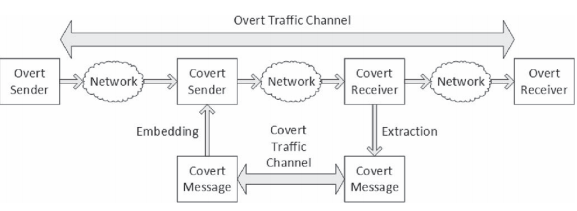
Table 8 summarizes the two main threats scenario, that have been considered, by distinguishing between storage- and timing covert channels along with related prevention approaches.
| Threat Scenarios | Prevention approaches |
| Storage Covert Channels |
– Mandatory Access Controls – Shared Resource Overflow – Bandwidth Reduction – System Analysis |
| Timing Covert Channels |
– Event-based mathematical models – Fuzzy time – Time-deterministic replay |
These are two low level threat scenarios that require very high skills in technical knowledge. In particular:
- Storage Covert Channels. Storage covert channels are more commonly used than timing covert channels as they are easier to implement. The sender embeds messages of bits in the object values which are read by the receiver. This works by mutual exchange of storage between processes. Resources like physical memory, shared hardware resources, I/O schedulers and queues for shared devices can be used as storage channels. For example, by taking a look at a printing queue: the higher security process exchanges messages with the lower security processes by sending a 1 or a 0 to the printer queue and the lower security process (the receiver) polls the queue to determine if it is full.
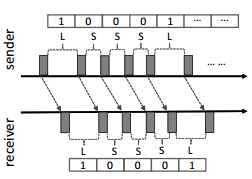
- Timing Covert Channels. Timing covert channels use a clock or measurement of time to signal the value sent over the channel. The sender manipulates the usage of communication resources conforming to message bits such that the receiver can rectify the message from the communication stream, which can include changing the rate of packet transmission or varying the message sizes according to the message to be transmitted (Cabuk, Brodley and Shields 2014). An example of a timing covert channel operating on packet transmission rate can be seen in Figure 3. The transmission rate is used to transfer certain bits.
They represent the most common way to protect the system. Performing a detailed analysis of the system frequently can uncover abnormal behaviour, e.g. monitoring running processes, sent messages and newly installed files that are unauthorized. Especially low security processes have to be monitored to prevent them from accessing higher security resources.
Typical prevention mechanisms in the scenario of storage covert channels are:
- Mandatory Access Controls allow the system to assign certain security features which cannot be changed on request. Only qualified actors who provide the necessary security attributes can access files and programs operating for the user cannot change their own security attributes or of any other file. It also prevents creating a shared file, and use it for passing through information (Zander, Armitage, and Branch 2007).
- Shared Resource Overflow restricts processes by limiting their quota to fill resources queues. Therefore, processes which appear too greedy are detected by the system and are prevented to allocate even more resources. If their quota is full, the requested resource is no longer shared between processes.
- Bandwidth Reduction is another prevention method. Noise is added to the channel to achieve a reduction in bandwidth. This can slow down the communication channel immensely (e.g. 17 min for 1 bit to transmit), which makes such a channel hard to realize.
Whereas prevention mechanisms in the scenario of timing covert channels are:
- Event-based mathematical models. In (Shrestha et al. 2016) an event-based mathematical model for generalizing and classifying timing covert channels, to help network wardens deal with time covert channels, is proposed. The approach calculates the capacity of covert channels and analyzes features like noise, performance and reliability. They proposed the network jitter model which interferes with the transmission times of the covert sender packets and cause the receiver to decode the message incorrectly, and the packet loss model. Timing covert channels react very sensitive to packet losses, which leads to decoding errors.
- Fuzzy time randomizes the length of the operating system tick interval and reduces the granularity of the system-wide time register (Zander, Armitage and Branch 2007). To address I/O clocks, fuzzy time randomizes the response time of requests, i.e., the time at which notification of the completion of an event occurs. The implementation of fuzzy time proved to be an extremely effective mechanism to prevent covert timing channels, hampering their usability measured by increase of noise and reduced throughput.
- Time-deterministic replay (Chen et al 2014) can reproduce the execution of a program, including its precise timing. It can be used to reconstruct what the timing of the packets should have been. Each machine is required to log its inputs; this log could then be examined periodically, perhaps authenticated, and then replayed with time-deterministic replay on another machine, using a known implementation of the examined machines software. The packet timing during replay should match any observations during play (e.g. from traffic traces) if no timing covert channel is present. Any significant deviation would be a strong sign of such a channel.
